Proxy is fast transforming into the reaction to various associations network concerns. Proxy takes the web to the accompanying level creation correspondence more useful through usage of a private association. The far off association made makes it possible to securely share data across distant regions. Proxy reviews from associations that usage this advancement give testimony regarding its benefits and reasonable centers, especially for affiliations that have laborers arranged in different zones. Regardless of the way that proxy can be adequately fought to be better than standard web, an enormous part of its inclinations depending upon the sort of proxy shipper that you have. There are various vendors in the market with strong proxy overviews, who offer a collection of organizations. Before you settle for any one there are different examinations that you need to consider.
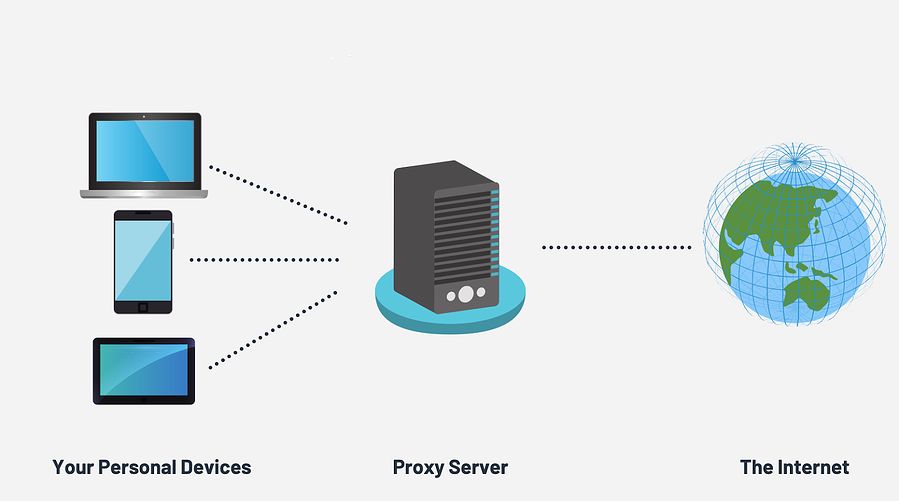
The chief idea that you need to make deals with your primary concern A couple of individuals need to make this decision last. At any rate it is fundamental to acknowledge precisely the sum you can spend. Proxy organizations come at different expenses depending upon the levels of safety that you require. If you experience proxy reviews you will consider that to be realistic helpers as this might put a broad engraving in your monetary arrangement. The second step in the process is to restrict exactly what you need. There are a couple proxies that you can peruse. PPTP, L2TP/IP and Open proxy these three surrender in the level of safety gave and the method of foundation. The first is the most easy to present, at any rate gives insignificant proportion of safety. According to strong proxy overviews the last two are secure, at any rate Open proxy anticipates that you should present additional client programming on your structure while L2PTP/IP does not and visit https://you-proxy.com/.
The third step includes taking a gander at their ability to meet your organization needs. This can be considered similar to openness of laborers. The introduction of your proxy is incredibly dependent upon the number similarly as the space of the specialists that your trader has. Considering that proxies support secure organization across critical distances you need to pick a provider that has laborers in the domain that you or your workers will get the web from. It is recommended that you check for data volume covers before you purchase proxy. Different proxies do not offer data volume covers which can baffle their presentation if various customers will overall download gigantic volumes of data. Taking into account proxy reviews, in case you are not in the recently referenced customer arrangement, by then you can benefit more from an proxy organization that puts a cutoff on data move volumes.



